Quick Links
Popular Searches


Close
Products
Support
Resources
Downloads
Company
At Quick Heal and Seqrite, Governance, Risk, and Compliance (GRC) is the structured framework through which cybersecurity responsibilities are defined, risks are identified and managed, and regulatory and contractual obligations are addressed.
Quick Heal delivers cybersecurity solutions for consumers and small businesses, while Seqrite serves enterprises, critical infrastructure, and government organisations. Both operate under a unified GRC approach focused on accountability, resilience, and trust.
A strong GRC framework enables:
GRC ensures cybersecurity is managed as a long-term organisational responsibility rather than a reactive technical function.
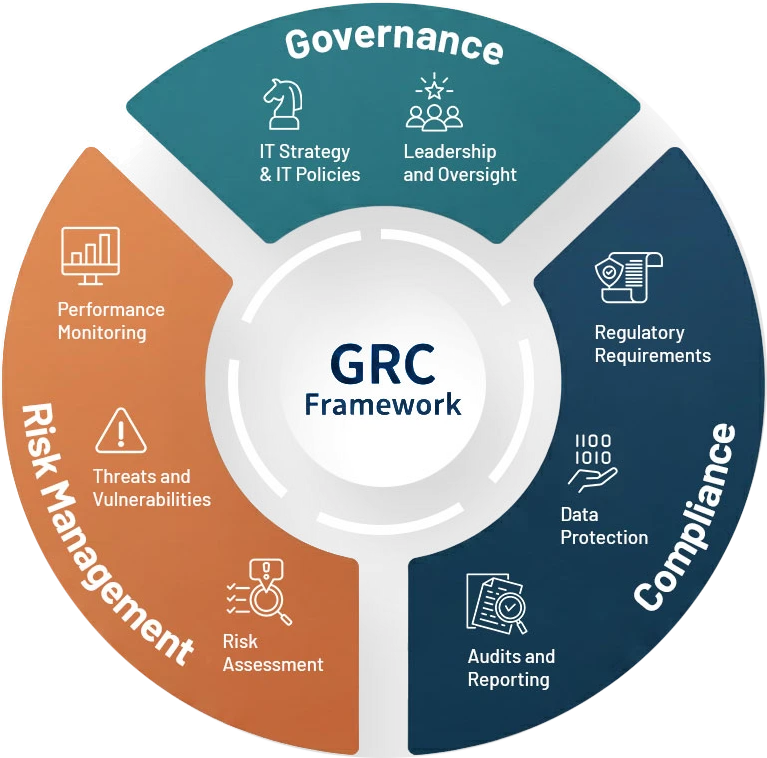
IT Strategy defines the long-term direction for how technology enables business objectives, while IT Policies establish the rules and standards for how IT systems are used, governed, and protected on a day-to-day basis.
Leadership and Oversight ensure effective governance by setting the “tone at the top,” assigning ownership for risk and compliance, and providing direction, supervision, and accountability across the organization.
A threat is a potential cause of harm, a vulnerability is a weakness that can be exploited, and risk arises when a threat exploits a vulnerability.
Risk Assessment is the structured process of identifying, analyzing, and evaluating risks that could impact business objectives, security, compliance, and operations.
Performance Monitoring measures how effectively governance, risk, and compliance controls operate in practice and whether they deliver the intended outcomes.
Regulatory Requirements are the laws, regulations, standards, and contractual obligations that the organization must comply with to operate legally, ethically, and responsibly.
Data Protection focuses on safeguarding personal, sensitive, and business-critical data through appropriate technical and organizational controls while meeting applicable legal and regulatory obligations.
Audits and Reporting provide independent assurance and transparency into the effectiveness of governance, risk management, and compliance controls.
Business Continuity is the organization’s ability to continue delivering critical products and services during and after disruptive events.
Accountability ensures clear ownership and responsibility for governance, risk, and compliance decisions and outcomes across the organization.
Integrity reflects a commitment to ethical, honest, and transparent conduct in managing governance, risk, and compliance activities.
Security encompasses the policies, controls, and practices that protect information, systems, products, and data from threats while ensuring compliance with applicable laws and standards.
Cybersecurity governance defines how security-related decisions are made, approved, implemented, and reviewed across the organisation.
The governance framework includes:
This governance structure supports both consumer-grade security at scale and enterprise-level control and visibility.
Yes. Quick Heal maintains documented Information Security Management Systems and Business Continuity policies that are:
Policy review frequency is defined internally and aligned with organisational governance and risk management practices.
Information security and business continuity policies are communicated internally through:
This ensures that employees understand their obligations related to security, continuity, and resilience.
Yes. Quick Heal provides internal training and awareness initiatives covering:
These initiatives reinforce compliance with internal policies and support a security-conscious organisational culture.
Quick Heal and Seqrite follow a structured enterprise risk management (ERM) approach aligned with ISO 31000 and COSO ERM frameworks.
Key Risk Categories We Manage:
Risk management activities include:
Yes. Quick Heal conducts risk assessments that consider:
Business Impact Analysis (BIA) for services offered to customers consider:
These assessments support resilience planning and informed decision-making.
Product and technology risks are managed through:
Performance, accuracy, and reliability considerations are balanced with security effectiveness, including optimisation for budget and resource-constrained devices.
Quick Heal and Seqrite align with applicable Indian and global standards and regulatory requirements, including:
Compliance obligations are integrated into governance, risk management, and operational processes.
Yes. Quick Heal has a designated role responsible for overseeing data privacy governance within the organisation.
This role supports:
The function operates within the broader governance and compliance framework.
Yes. Quick Heal maintains documentation, including Data Flow Diagrams (DFDs), that describe how data moves across systems and services.
These diagrams support:
DFDs are prepared and maintained as part of internal governance processes.
As a cybersecurity provider, Quick Heal recognises its responsibility to protect customer data through secure, transparent, and responsible practices.
Depending on the product or service, limited categories of data may be processed, such as:
No personal communications, messages, file contents, or unrelated user content are parsed or stored. Data unrelated to cybersecurity operations is not collected.
Customer data is used strictly for:
Customer data is not used for advertising profiling or unrelated commercial purposes.
Customer data is protected using technical and organisational safeguards, including:
No messages or user details are parsed or stored on the server or local device. Quick Heal Does Not have access to any message, OTP, or personal information in any format. Data at rest and data in motion are encrypted. We are SOC2 & ISO27001:2022 (2022 covers data privacy & threat prevention) certified.
All message parsing happens only at the device level — no parsing takes place over the internet. During parsing, the app only looks for URLs and OTP patterns (regex).
If a URL is detected, only the URL is sent to the server for verification. At no point are the message contents read, transmitted, or stored — either locally or over the internet.
Data at rest and data in motion are encrypted. We are SOC2 & ISO27001:2022 (2022 covers data privacy & threat prevention) certified.
Access is restricted to authorised personnel with legitimate business needs.
Customer data is retained:
Data that is no longer required is securely deleted or anonymised.
Yes. Limited Personally Identifiable Information (PII) is stored on Quick Heal Activation Servers strictly for product activation and license management purposes.
The following information may be stored in encrypted form:
These details are required solely to enable product activation, license validation, and license transfer services. No PII is stored in plain text.
All data at rest and data in transit are encrypted, and access is restricted through controlled, role-based mechanisms.
PII handling and storage practices are aligned with applicable data protection regulations, including the Digital Personal Data Protection (DPDP) Act, 2023 (India), and GDPR.
Quick Heal’s information security and privacy controls are independently validated through SOC 2 and ISO/IEC 27001:2022 certifications, which include controls related to data protection, privacy, and threat prevention.
Customer data may be shared only under controlled circumstances, such as:
Customer data is not sold.
Customers may:
Clear processes exist to handle such requests.
Whether protecting individual users or supporting large-scale digital ecosystems, Quick Heal and Seqrite remain committed to strong governance, proactive risk management, regulatory responsibility, and respect for customer privacy.

Please complete your information below to login.