Tech Support Scams: A Comprehensive Guide to Cybersecurity Awareness
In our increasingly digital world, cybersecurity threats continue to evolve and multiply, targeting both individuals and organizations with sophisticated schemes designed to steal money and sensitive information. Among these threats, tech support scams have emerged as one of the most persistent and financially damaging forms of online fraud. With losses from these scams reaching over $1.4 billion in 2024 alone according to the FBI’s Internet Crime Complaint Center, and over 37,560 complaints filed in 2023 resulting in nearly $1 billion in losses, understanding and recognizing these scams has never been more crucial
Tech support scams represent a particularly insidious form of cybercrime because they exploit people’s trust in technology companies and their natural desire to keep their devices secure. These scams have evolved significantly since their inception, transforming from simple cold-call operations to sophisticated multi-channel attacks that leverage pop-up ads, fake websites, and even social media platforms to reach potential victims

The Anatomy of a Tech Support Scam
Tech support scams are a form of fraud designed to trick users into believing their device has a serious problem. Scammers then exploit this fear to steal money and sensitive data. Their process typically unfolds in three distinct stages.
Stage 1: The Bait (Initial Contact)
The scam begins by creating a false sense of urgency through unsolicited contact. This is achieved via several methods:
- Deceptive Alerts: Loud, flashing pop-up ads or full-screen warnings triggered while browsing unsecure websites, torrents, or clicking malicious links. These are often designed to mimic official system messages and include fake technical error codes or a toll-free number to call for “immediate assistance.”
- Scam Calls Posing as Employees: Fraudsters may call claiming to be from Microsoft, Apple, or even local ISPs. They often spoof caller IDs and sound professional, using fake employee names and ID numbers to build trust, while warning you of imaginary issues like malware, hacking, or data theft.
- Manipulated Search Results: Fake tech support websites that pay for top placement in search engine results.
- Phishing: Emails or social media messages that warn of a security issue and direct the user to a fraudulent link or number.
Stage 2: The Con (Building False Trust)
Once contact is made, the scammer uses social engineering to establish credibility and “prove” the non-existent threat. They pose as certified experts, using technical jargon and fake employee IDs. The core of the con involves guiding the user to legitimate system utilities, like the Windows Event Viewer, and misrepresenting normal operational logs and warning icons as definitive proof of viruses, hacking, or critical system failures. This theatrical “diagnostic” is designed to convince the victim that paid intervention is necessary.
Stage 3: The Heist (Exploitation & Theft)
With the victim’s trust secured, the scammer proceeds to the final exploit. This stage has two primary goals:
- Financial Theft: The user is convinced to pay for a “repair” or “protection plan,” with fees often ranging from $99 to over $1,000. Payment is demanded through untraceable methods like gift cards, wire transfers, or cryptocurrency.
- Data Theft: The scammer persuades the user to install remote access software (e.g., TeamViewer, AnyDesk), giving them full control of the computer. With this access, they steal sensitive data, including passwords, banking information, and personal files, which can be used for identity theft or sold on the dark web.
How Quick Heal Anti-Fraud Helps Prevent These Scams
Quick Heal’s advanced security features are designed to break the scam cycle at multiple points—detecting fraud early, preventing risky behaviour, and alerting users before any harm is done.
Stage 1: The Bait (Initial Contact)
- Fraud Call Alerts: Quick Heal’s mobile protection suite includes call detection systems that warn users of known scam numbers in real-time.
- Scam Website Blocking: When users visit malicious sites Quick Heal automatically blocks access and displays a clear warning.
Stage 2: The Con (Building False Trust)
- Screenshare Detection Alerts: If remote access tools like TeamViewer or AnyDesk are launched, Quick Heal can flag such behavior, warning users during active calls or sessions.
Stage 3: The Heist (Exploitation & Theft)
- Payment Protection Alerts: Banking Fraud Alert instantly detects suspicious calls and alerts you in an ongoing conversational call, which could lead to financial fraud. Fraudsters often trick people into sharing sensitive information like OTPs when on call, resulting in financial loss.
- OTP Alert to Trusted Buddy: Fraud Protect Buddy enables you to add loved ones who may be susceptible to fraud. This feature safeguards your loved ones from financial fraud by alerting you to the suspicious calls they receive.
- Data Backup & Restore: If a scammer gains access and attempts to corrupt your data, Quick Heal’s Backup & Restore feature ensures your important files remain protected. It allows you to securely create and manage backups, acting as a safeguard against data loss from threats like ransomware.
Case Studies: Tech Support Scam Operations in India
Operation Chakra Series:
The Central Bureau of Investigation (CBI) has conducted multiple large-scale operations targeting tech support scam centers across India. In Operation Chakra-II alone, authorities raided 76 locations across 12 Indian states, seizing 32 phones, 48 laptops and hard discs, and 33 SIM cards while freezing numerous bank accounts.
Source: https://staysafeonline.in/concept/tech-support-scams/case-study
Noida Operation (2025):
In a recent high-profile case, the CBI busted an international tech support scam syndicate operating from Noida, working in coordination with the FBI, UK’s National Crime Agency, and Microsoft Corporation. The operation, known as FirstIdea, targeted victims in the United Kingdom and Australia, with fraudsters caught in the act during live scam calls.
Source: https://staysafeonline.in/concept/tech-support-scams/case-study
West Delhi Brothers Case:
A particularly notable case involved two brothers operating from West Delhi who duped over 20,000 Americans out of $10 million over nearly a decade. Their operation used sophisticated pop-up advertisements to warn targets about fraudulent activity, then connected victims to their call Center where young employees, armed with well-rehearsed scripts, convinced victims to pay for fake computer repairs.
Source: How Delhi brothers duped 20000 americans in 10 million scam
The Scale of Operations
Financial Impact: Research indicates that a single pop-up campaign spread across 142 web domains brought in nearly $10 million in just two months, highlighting the lucrative nature of these operations. The FBI estimates that over 32,000 people were targeted by tech and customer support scams in 2022, with over $800 million in losses.
Organizational Structure:
These scam operations often function like legitimate businesses, complete with:
- Professional call centers with multiple workstations
- Scripted training programs for employees
- Sophisticated technical infrastructure for creating convincing pop-ups and fake websites
- Money laundering networks using “mule accounts” rented from individuals across different regions
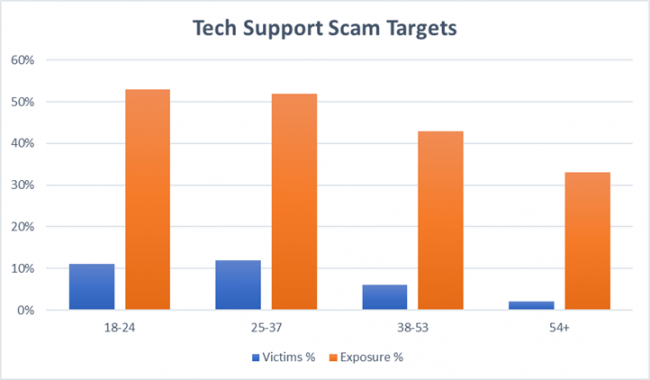
Tech Support Scam Vulnerability by Age Group
A Guide to Identifying Tech Support Scams: Key Warning Signs
Tech support scams are a prevalent form of cyber fraud that uses psychological manipulation to feign computer problems. Recognizing the distinct warning signs is the most effective defence. This guide outlines the key indicators across communication, technical, and financial interactions.
I. Communication Indicators
- Unsolicited Contact: The scam begins with the fraudster initiating contact. Legitimate tech companies do not make unsolicited calls or send messages about computer errors.
- High-Pressure Tactics: The use of aggressive, urgent language is common, threatening data loss or system failure to provoke immediate, uncritical action.
- Poor Professionalism: Scam communications often contain obvious spelling mistakes, grammatical errors, and unprofessional phrasing.
II. Technical & Tactical Indicators
- Generic On-Screen Alerts: Pop-up warnings are typically vague (e.g., “Virus Detected!”) and designed to lock the browser. Critically, these scam alerts often include a phone number, which legitimate system messages never do.
- Misuse of System Tools: A common tactic is to direct the user to legitimate utilities like the Windows Event Viewer, misrepresenting normal system logs as evidence of critical errors.
- Demand for Remote Access: An unsolicited request to install software (like TeamViewer or AnyDesk) and grant remote control of a device is a primary goal of the scam.
III. Financial Indicators
- Unconventional Payment Methods: A demand for payment via untraceable methods is the most definitive red flag. This includes gift cards, wire transfers, and cryptocurrency.
- Excessive Costs & Upfront Payment: Scammers often demand hundreds or thousands of dollars for worthless services and insist on payment before any “work” is performed.
- Impersonation & Evasion: Fraudsters will claim to be from well-known companies like Microsoft or Apple. However, they will become evasive or hostile if asked for verification or if the user offers to call back through an official company number.
Ultimately, tech support scams rely on inducing panic to bypass rational judgment. A skeptical approach and awareness of these patterns in communication and financial requests are the primary defences against such fraud.
Fell for a Tech Support Scam? A 3-Step Recovery Plan
Falling victim to a tech support scam can be stressful and alarming. If you suspect you’ve been scammed, taking immediate, decisive action is crucial to protect your information and finances.
Step 1: Secure Your Digital Life (Immediate Actions)
Your first priority is to lock the scammers out of your devices and accounts.
- Disconnect and Scan: Immediately disconnect your computer from the internet to terminate the scammer’s remote access. Afterwards, run a full system scan with a reputable antivirus program like Quick Heal to detect and remove any malicious software they may have installed.
- Change Critical Passwords: At once, change the passwords for your primary email, banking, and social media accounts. Use strong, unique passwords for each service and enable multi-factor authentication (MFA) wherever possible for an essential layer of security.
Step 2: Protect Your Finances (Financial Recovery)
Act quickly to prevent or reverse financial losses.
- Contact Your Bank and Credit Card Issuers: If you shared financial details or made a payment, call your bank’s fraud department immediately. Report the transaction, cancel any compromised cards, and ask if a chargeback is possible.
- Freeze Your Credit: To prevent scammers from opening new accounts in your name, consider placing a freeze on your credit reports with bureaus like CIBIL, Experian, and Equifax.
Step 3: Report the Crime (Documentation & Reporting)
Reporting the scam helps authorities track criminals and prevents others from becoming victims.
- Document Everything: Gather any evidence you have, including screenshots of pop-ups, fraudulent email addresses or phone numbers, and any transaction records.
- File an Official Report: In India, report the incident immediately through the National Cyber Crime Reporting Portal at https://cybercrime.gov.in/ or by calling the cybercrime helpline number 1930. You should also file a report with your local police station.
- Notify the Impersonated Company: Report the incident to the actual company (e.g., Microsoft, Apple) whose name the scammers used.
Moving Forward: Prevention and Awareness
- Embrace Healthy Skepticism: The number one rule is that legitimate technology companies will never contact you first about a problem with your device. Reject all unsolicited offers of “help.”
- Practice Good Cyber Hygiene: Maintain strong, unique passwords managed through a password manager, keep your software and operating system updated, and think before you click on links or attachments in unexpected emails.
- Stay Aware of Evolving Threats: Be mindful that scammers are now using Artificial Intelligence (AI) to create more convincing phishing emails and fake content. A security-first mindset is more important than ever.
By acting quickly to secure your accounts, protect your finances, and report the crime, you can significantly limit the impact of a scam.








