
Jul

Crypto Mirage: Unmasking the Billion-Dollar Illusion of Investment Scams
-
Subhrojyoti Chowdhury / 7 months
- July 24, 2025
- 0
A Cryptocurrencies have revolutionized the financial landscape, offering unprecedented decentralization, transparency, and autonomy. However, this innovation has also given rise to a surge in sophisticated scams and fraudulent activities. To better understand this phenomenon, we’ll explore the evolution, patterns, losses, and mitigation strategies associated with cryptocurrency and investment scams.
The Evolution of Cryptocurrency Scams :
As cryptocurrencies like Bitcoin and Ethereum gained popularity, scammers saw an opportunity to exploit anonymity and lack of regulation. Initially, scams were relatively simple, involving phishing attacks and Ponzi schemes. However, as the market grew, so did the complexity and sophistication of scams. Today, scammers use advanced tactics like fake ICOs (Initial Coin Offerings), phishing attacks, Ponzi schemes, and fake cryptocurrency exchanges.

Scam Data And Trends :
Imagine losing billions to scammers in just half a year – that’s exactly what happened in 2025, with over $2.5 billion gone. The Bybit hack was a massive blow, swiping $1.5 billion. And here’s the kicker: stablecoins are increasingly being used for these shady deals.
The numbers are mind-blowing. Since 2020, crypto scam losses have shot up from $7.8 billion to a whopping $26.4 billion in 2024. And it’s not showing any signs of slowing down. Americans lost a staggering $1.5 billion in just three months this year. If you fall victim to a scam, you could be out around $39,000.

| Year | Total Crypto Scam Losses (USD) |
| 2020 | $7.8 Billion |
| 2021 | $14.6 Billion |
| 2022 | $17.9 Billion |
| 2023 | $24.2 Billion |
| 2024 | $26.4 Billion (est.) |
Classification of Crypto Scams :
-
- Ponzi Schemes: These scams pay old investors with new investors’ money, promising crazy returns. But when the new investors dry up, the whole thing collapses. Bitconnect’s $2.4 billion collapse is a prime example.
-
- Rug Pulls: Developers hype up a project, get investors on board, and then vanish with the funds. Thodex and SushiSwap are notorious examples, leaving investors with huge losses.
-
- Phishing Attacks: Scammers create fake websites or social media profiles, tricking victims into revealing sensitive info like wallet keys or passwords. Twitter and MetaMask clones have been used to steal user credentials.
-
- Pump & Dump: Scammers artificially inflate a cryptocurrency’s price with false hype, then sell their holdings, causing the price to crash. Telegram and Reddit groups have been used to coordinate these schemes.
-
- Fake ICOs: Scammers create fake projects or products, sell tokens to investors, and often have no intention of delivering. Centra Tech, endorsed by Floyd Mayweather, is a shocking example. Stay vigilant, and don’t fall for the hype!

Case Studies :
-
- A UK businessman allegedly ran a massive £330 million Ponzi scheme with TradeAI/Stakx, promising investors huge returns from AI-powered trading. But it was all a lie.
Source: The Times (UK)
-
- In Spain, Europol cracked down on a huge money laundering operation that had laundered €540 million. It’s mind-boggling to think about the scale of these crimes.
Source: Reuters
-
- An elderly couple in Texas lost their entire retirement fund of $270,000 to scammers who built trust and then drained their account. It’s heartbreaking.
Source: KFOX14 / CBS4 News (USA)
-
- The WazirX hack in India was a major security breach, with the Lazarus Group stealing $234.9 million using social engineering tactics. It’s a stark reminder to stay vigilant.
Source: Wikipedia
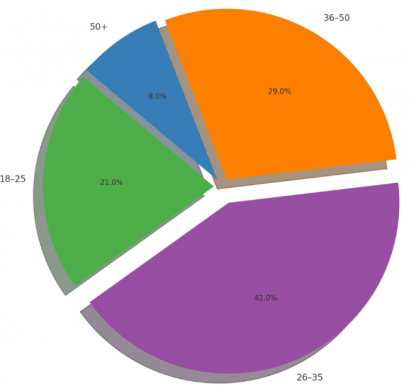
Age Groups Affected :
Tools for Scam Detection:
| Tool | Purpose |
| Chainalysis | Blockchain flow tracking |
| Elliptic | Wallet risk ratings |
| MetaMask + ScamSniffer | Detect phishing URLs |
| Google Trends | Detect scam wave sentiment |
| Python + Pandas | Custom behavior modeling |
Legal & Regulatory Status:
| Region | Regulatory Body | Key Actions |
| USA | SEC, CFTC, DOJ | Prosecute crypto crimes |
| India | RBI, ED | Restrict unregulated exchanges, probe fraud |
| EU | MiCA | Regulate assets, KYT, AML norms |
Challenges:
| Challenge | Description |
| Decentralized Exchanges/Mixers | Scams utilize decentralized platforms, making tracking difficult |
| Cross-Border Enforcement | Lack of treaties hinders international cooperation and enforcement |
Fake Cryptocurrency Trading Website showing fake Returns and Growth
A minimal Python script that detects phishing-style crypto URLs by checking for brand misuse and abnormal subdomain structure. Not meant for enterprise-grade protection.
Your Security Check List:
| Category | Recommendation |
| Individuals | Avoid “guaranteed returns” |
| Don’t trust unsolicited DMs or investment pitches | |
| Use cold wallets for storage | |
| Companies | Implement AI-based fraud detection |
| Educate users with phishing simulations | |
| Mandate KYC/AML at exchanges | |
| Governments | Build public scam reporting portals |
| Deploy blockchain forensic teams | |
| Collaborate on global crypto regulation |
Quick Heal Anti-Fraud AI Features tackling Crypto Frauds:
| Feature | Description |
| Real-Time Phishing Detection | Detects malicious URLs, domains, and fake trading platforms. Blocks phishing sites mimicking crypto exchanges/wallets. |
| Behavioral Heuristics | Analyzes suspicious browser behaviors (e.g., wallet hijacking, pump-and-dump schemes, auto-mining scripts). |
| AI-Based Email/SMS Filtering | Flags scam emails/texts with fake wallet addresses, returns, or “crypto doubling” claims. |
| Threat Intelligence Integration | Leverages global threat intelligence to blacklist wallets, IPs, and scam sites. Alerts on known scam interactions. |
| Malicious Crypto Miner Detection | Detects background crypto mining scripts (cryptojacking) hidden in investment sites or fake apps. |
Conclusion:
Investing in cryptocurrency and other assets requires a cautious approach, as scammers often exploit unsuspecting individuals through phishing schemes and dubious investment opportunities. It is crucial to exercise due diligence and thoroughly research potential investments to avoid falling prey to such scams.
By adopting a vigilant and informed stance, investors can mitigate potential risks and make well-informed decisions. This includes verifying the authenticity of investment opportunities, being wary of unsolicited offers, and diversifying portfolios to minimize exposure to potential losses.






